Deploying Intune (MEM) to existing devices in your environment can sometimes be a slow process. You first have to Hybrid AAD join them all, then deploy either SCCM Co-management or the GPO, and then have all of the various scheduled tasks runs to complete the process.
It can take a long time.
Plus, there may actually be errors or issues blocking enrollment from completing. Today, I’ll be showing you some ways to remotely speed up the Intune enrollment process. Additionally, it will give you way to remotely troubleshoot as well.
Table of Contents
- Pre-Reqs
- Understanding the Basics of Enrollment
- Fixing Intune Enrollment Remotely
- Use PSExec
- Fixing Hybrid Join Remotely
Pre-Reqs
This process will only work if you have the following in place:
- Ability to administratively run remote PowerShell on clients (WinRM enabled)
- Administrator access to clients
- Enabled Hybrid Join and SCCM Co-Management and/or GPO for Intune Enrollment
In my case, I’ll be primarily writing from the Hybrid Domain Join + SCCM Co-management perspective as that is what I have in my environment.
Understanding the Basics of Enrollment
After you enable automatic Intune enrollment in SCCM co-management (either “Pilot” or “All”), the clients will get the “MDM Enrollment URL” from SCCM (https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc) and attempt to enroll.
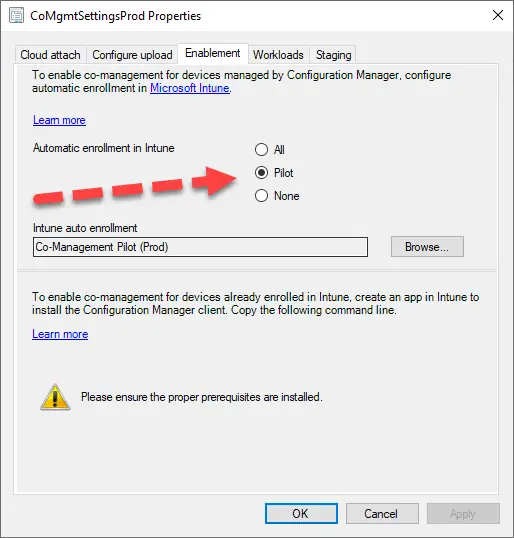
You can watch the process in the “C:\Windows\CCM\CoManagementHandler.log”.
The problem is that you have very little control over when exactly SCCM “triggers” the MDM enrollment. It can be scheduled for some arbitrary time in the future, waiting for reboot, etc.
If you use GPO method, it at least gives you a scheduled task to work with — “MDM MaintenenceTask” and then makes it a little easier to remotely trigger.
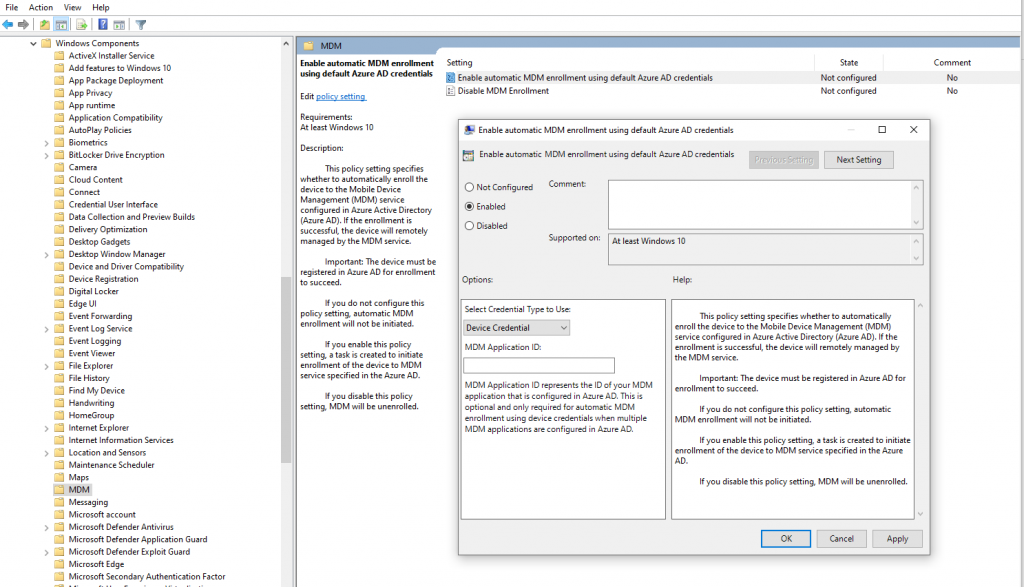
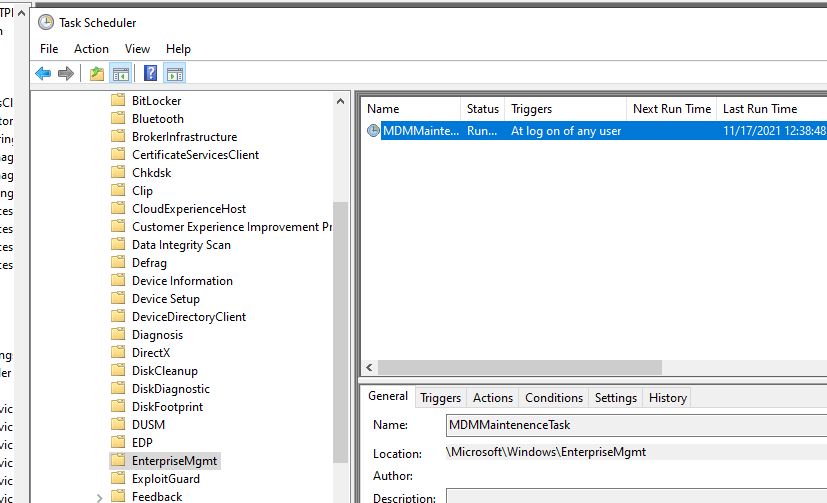
Either way, how do we speed things up?
Fixing Intune Enrollment Remotely
The following is the basic process for remotely triggering Intune enrollment:
- Launch PowerShell as an administrator that has remote access to the PC you are targeting
- Create a variable say $computername that will contain the target computer. You may need to use FQDN depending on DNS.
- Run various one line or multi-line “Invoke-Command” commands in PowerShell, depending on what you need to do.
Here’s what I mean. First, set the computer name:
$computername = "Desktop-180G3D2"Then I like to query the OMA-DM logs to see what is going on. Note you can tweak the “-MaxEvent” value depending on how far back you want to see.
Invoke-Command -ComputerName $Computername -Command {Get-WinEvent -LogName "Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin" -MaxEvents 100 |sort TimeCreated | ft -AutoSize -Wrap}On one problematic system, I can see that it has Device Credential errors.
‘Auto MDM Enroll: Device Credential (0x1), Failed (Unknown Win32 Error code: 0x80192ee2)”
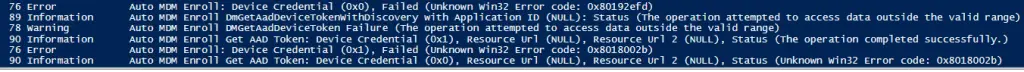
In my environment, this issue is usually related to proxy configuration. More often than not I need to set the system level winhttp proxy and then retry the process:
Invoke-Command -ComputerName $Computername -Command {netsh winhttp set proxy proxy.contoso.com:8080}After I set the proxy, I need to retry Intune enrollment. Since SCCM is the one enabling auto-enrollment, I need to trigger it with SCCM. The easiest way I’ve found to do this is just to restart the ccmexec service.
Invoke-Command -ComputerName $Computername -Command {restart-service ccmexec}Wait 2-3 minutes or so and check OMA-DM log again. Oh look, the device can successfully authenticate to Intune now with Device Credentials.
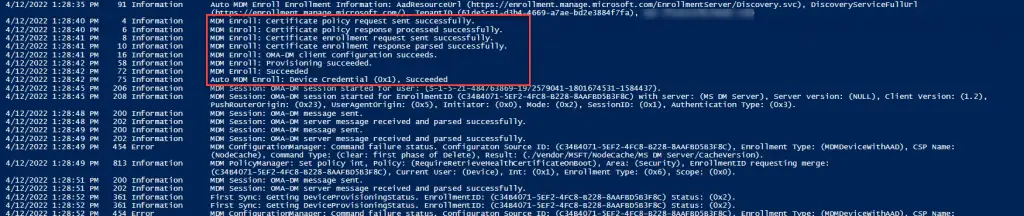
If you check the CoManagementHandler.log, you should see success as well.
You can deploy all of these command in a block as well:
$computername = "Desktop-180G3D2"
Invoke-Command -ComputerName $Computername -Command {
netsh winhttp set proxy proxy.contoso.com:8080
restart-service ccmexec
sleep -seconds 120
Invoke-Command -ComputerName $Computername -Command {Get-WinEvent -LogName "Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin" -MaxEvents 40 |sort TimeCreated | ft -AutoSize -Wrap}
}Use PSExec
If you have the ability to run PSEXEC, then this can also work to remotely trigger the Intune enrollment process. Under the hood, Windows uses c:\windows\system32\deviceenroller.exe to actually do the MDM enrollment. This executable doesn’t have a UI or even any information on what switches are available. You can google around for more info on this, but essentially this is the basic command:
c:\windows\system32\deviceenroller.exe /c /AutoEnrollMDM
The trick is that this has to be run as the SYSTEM account. So to do that with PSEXEC, you can run this command:
C:\temp\PSTools\PsExec.exe "\\$computername" -accepteula -s cmd /c c:\windows\system32\deviceenroller.exe /c /AutoEnrollMDMThis page from Microsoft goes into a lot more detail on how this all works and it’s worth a read.
Fixing Hybrid Join Remotely
I’ve run into other issues where the clients are getting stuck on the Hybrid join process also due to proxy misconfiguration. I ended up having to remote the IE proxy configuration for the local system account.
Run this command to check the Hybrid join status:
$computername = "Desktop-180G3D2"
Invoke-Command -ComputerName $Computername -Command {dsregcmd /status}Then we can check the SYSTEM IE proxy settings:
Invoke-Command -ComputerName $Computername -Command {bitsadmin /util /getieproxy localsystem}Here, a proxy pac autoscript file is configured.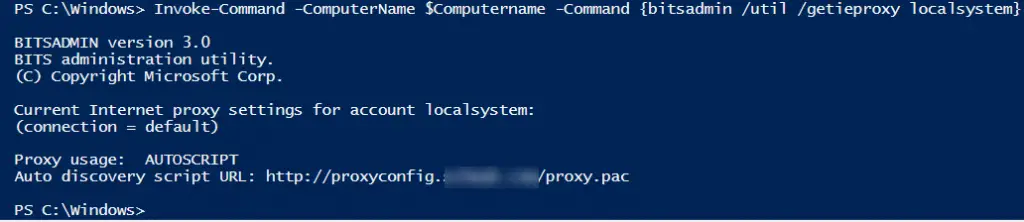
I don’t want that configured as it is impacting computer object authentication. I can reset this configuration by running:
Invoke-Command -ComputerName $Computername -Command {bitsadmin /util /setieproxy localsystem NO_Proxy}If you instead wanted to actually set the IE proxy here in case it wasn’t set you can run:
Invoke-Command -ComputerName $Computername -Command {bitsadmin /util /setieproxy localsystem AUTOSCRIPT http://proxyconfig.contoso.com/proxy.pac}You may want other types of configuration here so be sure to check Microsoft’s documentation page for the other switches.
If you are curious, this command sets the Internet Explorer proxy settings under Internet Properties > Connections Tab > LAN Settings. Keep in mind this is for the SYSTEM account and you won’t be able to view that in the UI unless you use PSEXEC as SYSTEM and then load “inetcpl.cpl”.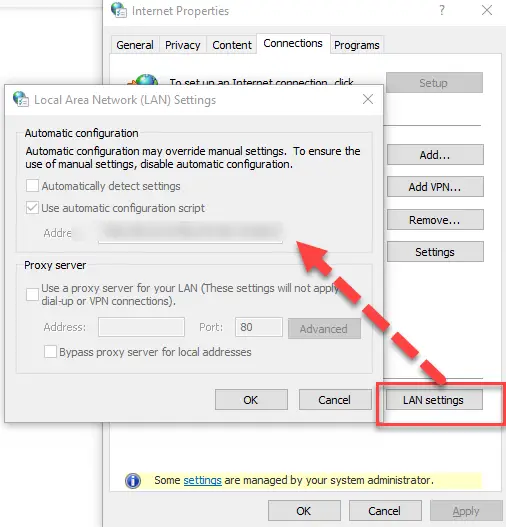
I decided to run all of the commands together in a block like this:
#Fix Hybrid Join
Invoke-Command -ComputerName $Computername -Command {
netsh winhttp reset proxy
bitsadmin /util /setieproxy localsystem NO_Proxy
dsregcmd /join /debug
Get-WinEvent -LogName "Microsoft-Windows-User Device Registration/Admin" -MaxEvents 20 | sort TimeCreated | FT -wrap
}And that did the trick and fixed my Hybrid Domain joined issues.
The sky is the limit on how much you can run remotely on systems using PowerShell. Once you’ve got the right commands working, you can add this is a script in SCCM or other deployment tool to help turbocharge Intune enrollment.