Microsoft Intune and VMware Workspace ONE are both industry-leading Unified Endpoint Management (UEM) solutions. If you look at any Gartner Magic Quadrant chart from the last few years and you’ll see both Microsoft and VMware competing for the top spot. But which one is actually better for your organization?
UEM is all about managing multiple operating systems and device types with a single management tool. Your salesperson probably calls this a “Single Pane of Glass”. The most common operating systems are of course iOS, Android, Mac, and Windows, but these tools can manage more operating systems than just those. In the last 6 years, I’ve focused extensively on managing Windows devices with Workspace ONE and Intune and so that’s where we’ll focus in this blog.
I’m going to detail 15 Pros and Cons of each solution based on my personal experience of each. For Workspace ONE, I’ve been a system administrator, an architect, a consultant, and even a product manager. For Intune, I’m been an architect/system administrator. My goal is to cut through the marketing and share what it’s really like to use both of these products in actual environments. I’ve seen the good, the bad, and the ugly, and want to share them with you!
Table of Contents
- Before We Begin
- Pros of VMware Workspace ONE
- Cons of Workspace ONE
- Pros of Microsoft Intune
- Cons of Microsoft Intune
- Conclusion
Before We Begin
Even though we’ll be focusing on Windows for this blog, there is so much to managing Windows devices in the enterprise. While I won’t be able to cover every aspect of what each tool can do, I’ll try to focus on the core aspects so that you can make a more informed decision around deciding on which tool to use for your organization.
Also, both of the products are consumed as a SaaS service and thus are constantly updated. This post is up-to-date as of the date of writing, but keep in mind that things may change.
Pros of VMware Workspace ONE
Let’s look at the main benefits of Workspace ONE.
SaaS Flexibility
Workspace ONE (WS1) as a platform is very easy to consume. Customers can choose between a shared or dedicated SaaS environment. In a shared environment, your WS1 instance shares resources with other tenants. Your data, settings, and configuration are fully segmented but you just don’t have dedicated resources. This is a cheaper option and perfectly fine for most customers. Additionally, you are automatically upgraded to the latest version when it becomes available. You don’t get to defer or choose which version you are on.
For larger customers who want their own dedicated environments, then “dedicated” SaaS is a good option. Dedicated SaaS has better performance for large environments and you also get the added benefit of controlling what version you are on. You can also set up Dev, UAT, and Prod instances– all fully separate. This makes testing and verifying compatibility (and bugs) easier.
Additionally, you can still deploy Workspace ONE on-premises although I wouldn’t recommend this. This is only for highly secure or legacy environments and adds a lot of overhead to you. Plus, you don’t get the benefits of new features that VMware releases for SaaS-only customers.
Speed of Console and Deploying Workloads
In my opinion, Workspace ONE has a snappier console and processes workloads faster than Microsoft Intune. It also reports back the status of a profile or application you just deployed. The main time it slows down is when a menu item flips into the “Modern” UI. VMware has been modernizing the code of various parts of the console and it will have to “load” that when you click into it. This split style of the console is a bit jarring, but I am glad they are focused on uplifting things to the modern UI.
Old UI:
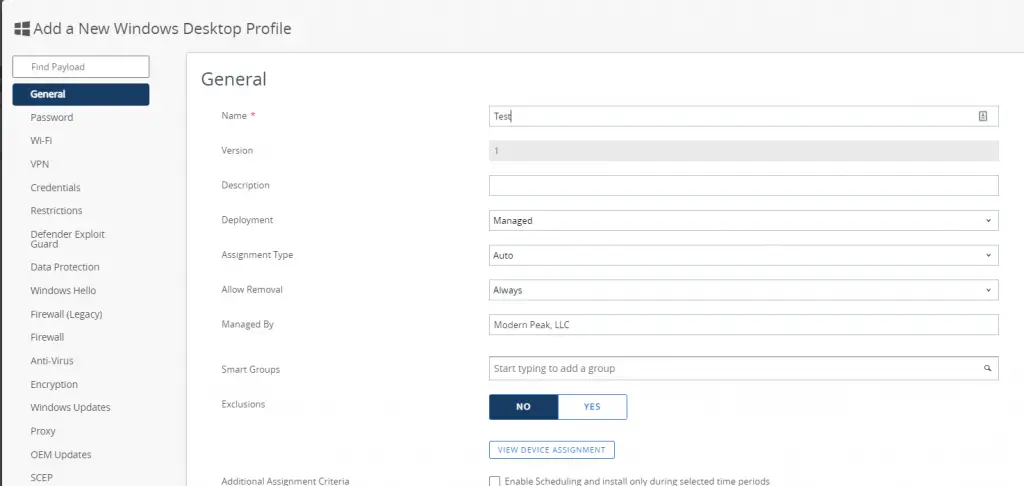
New, Modern UI:
Additionally, I find that pushing profiles or apps to devices happens very quickly assuming there aren’t issues with it. Things can get stuck if you misconfigure something or have an incompatibility somewhere. Also, the console does slow down as the environment grows and more content is added.
Software Distribution
Workspace ONE has a fairly robust software distribution platform. You can directly upload MSI or EXE files and the console will accept them. For MSIs, the console will even automatically populate some of the metadata for you such as version. You can also upload bundles of content in a zip file — just make sure you include at least one MSI or EXE in there as it will check. Once uploaded, you can customize the app including changing the icon, categories, command line, and more.
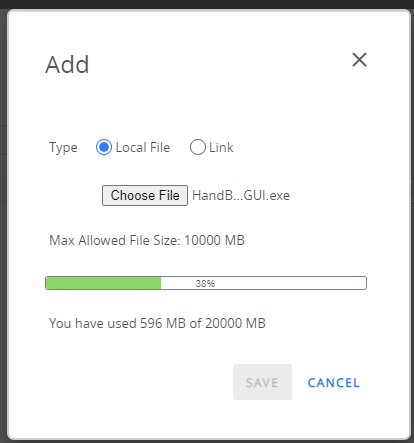

If you don’t want to upload your own apps, you can take advantage of the Enterprise App Repository (EAR). This is a software “catalog” that includes many common applications such as Notepad++, Office 365, and Firefox. They have partnered with a third-party company in the background to seed all of those applications including the binaries and application details.
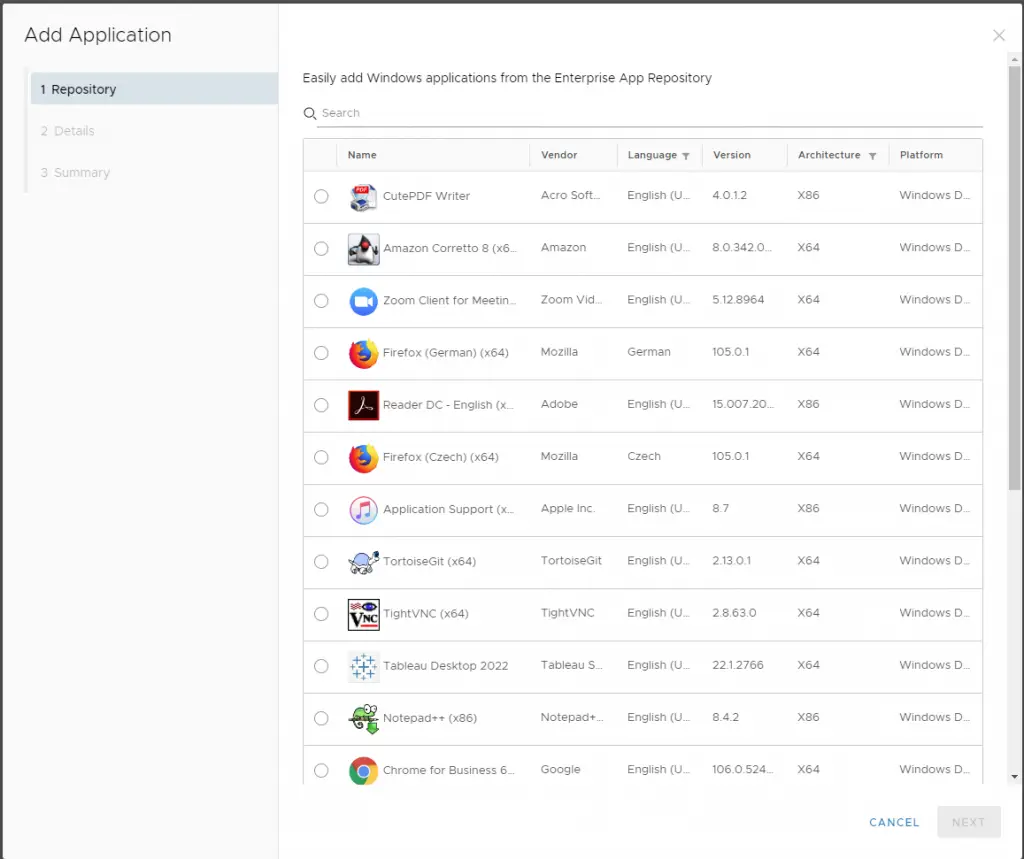
Once an app is uploaded or added from the EAR you can then customize the assignment. This is where you will add assignment groups (also called “smart” groups), set the priority level on each, and configure the deployment type: auto or on-demand. “Auto” means the app gets pushed automatically and “On-Demand” means the app is available for the end user to install from the Hub. Additionally, “On-Demand” apps can be pushed to individual devices from the console, which I find to be very useful.
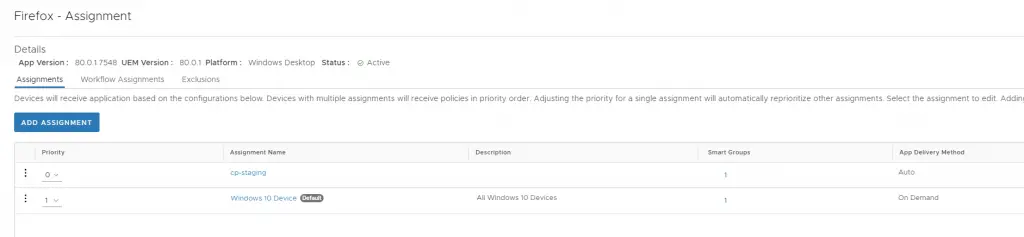
There are a few other app configurations worth noting:
- Hide Notifications – Suppresses Windows toast notifications
- Allow User Install Deferral – Will accept deferral exit codes used by tools such as PowerShell App Deploy Toolkit (PSADT)
- Show or Hide in the App Catalog (Intelligent Hub)
- Set Reboot Handling
- “Take Over” management of an app if it is already installed on the system. If the “detection criteria” matches that of an app already installed it will assume management of it and mark it as installed in the console.
- Desired State Management – Enabling this keeps the apps installed, even if it gets uninstalled by the end user.
Software Distribution is a critical piece of any management toolset and here I think Workspace ONE does it well. Most organizations will find it’s “good enough” even if it’s not as granular as some other tools. But it’s not perfect and I do have a few issues with it (see Con section).
Scripts, Sensors, and PowerShell
WS1 has grown in the area of supporting native PowerShell in the console. Early on, doing PowerShell was a challenge, and deploying a simple “script” involved building a whole application just for it. Recently they have released a new way to deploy scripts natively.
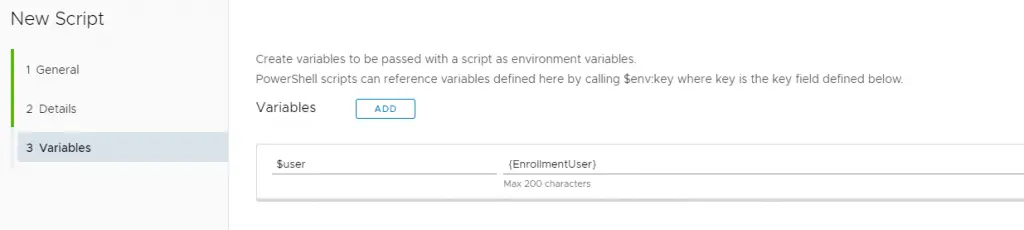
You can navigate to Resources > Script to upload a PowerShell script file or copy/paste the content directly. You can also set up variables that can be passed into the script by the WS1 Agent. Neat!
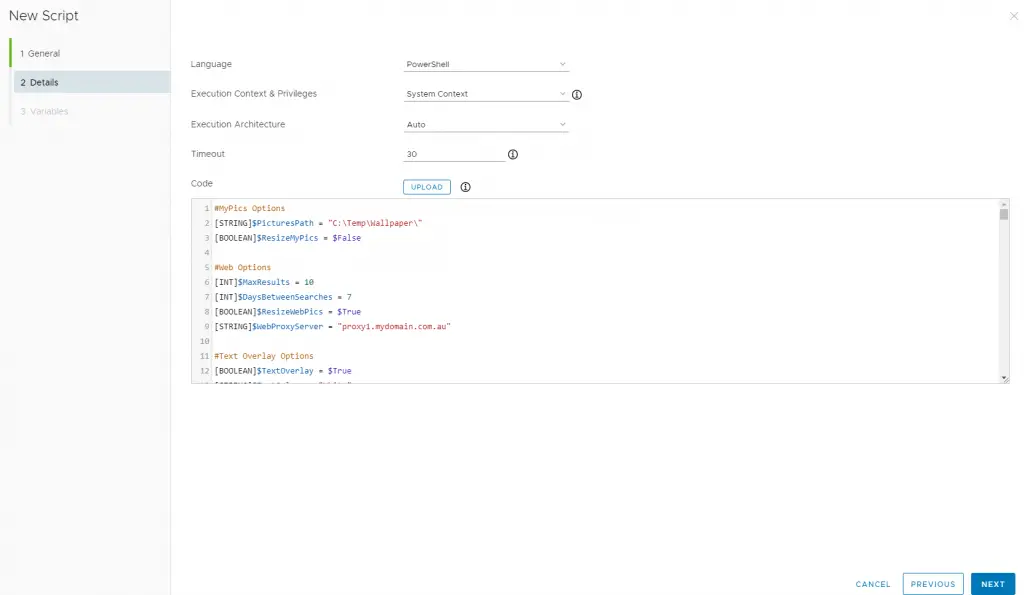
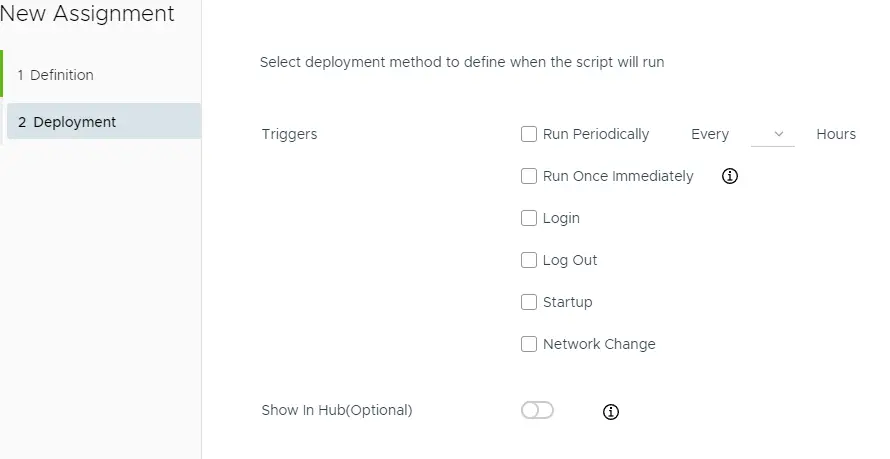
Scripts can then be configured to run once or on different schedules.
Sensors are a different type of object in WS1 and they are used to “query” data on the device. You write them yourself in PowerShell to query a specific property on the device. Some examples would be things like timezone, free disk space, IP address, etc. Accessing the data returned by sensors was previously a Workspace ONE Intelligence exclusive feature, but they have since expanded it to show the data right on the device details page.
Intelligent Hub
The Workspace ONE Intelligent Hub is the primary end-user application that enables self-service, company branding, and a unified app catalog. This leverages “Hub Services” from the UEM console and brings a number of different things together into one place. For Windows devices, it allows the end user to install any application published to them. It also will show published virtual apps or virtual desktops. Additionally, it can show help desk information and even corporate messages.
Overall it’s a pretty good application with a modern feeling UI. It is fairly complex under the hood and needs healthy communication between Workspace ONE Access and UEM to function properly. The look and feel extends to other platforms and even in the browser.
BitLocker
BitLocker management with Workspace ONE is solid and has all the features you need at an organization. This is often one of the first workloads most customers turn on when starting out. This is deployed as a “Profile” but do note that this isn’t using the same BitLocker CSP that Intune uses. The settings are sent directly to the Workspace ONE hub and it then calls the various BitLocker commands (manage-bde) to apply them. It has core functionality such as encryption of the Operating System and Fixed drives with the various encryption methods, leveraging TPM and/or PIN, enforcing encryption, encrypting used space on initial encryption, and configuring the URL for the recovery screen.
It has a few features that Intune doesn’t have such as:
- Force Encryption – This is a super aggressive form of enforcing encryption and the Hub will immediately turn BitLocker protection back on if it gets suspended.
- Keep System Encrypted at all times – this keeps the system encrypted even if the profile is removed or the device becomes unenrolled.
- Static Recovery key: you can have it add additional recovery keys on every device that are the same. These are like “administrative” keys that get set and rotated every now and then. While it sounds cool, I’ve not seen this used very much in practice.
Enrollment Methods
Workspace ONE has a variety of enrollment methods that suit many use cases in an enterprise environment. Workspace ONE isn’t coupled to an identity directory like Intune is to Azure Active Directory. So this can give you more options to get devices enrolled. Here are the primary methods:
- Intelligent Hub Driven – This is primary for BYOD use cases. The user downloads and installs the WS1 Hub and walks through the screens to enroll their device with their corporate creds. This would be marked as “Employee Owned” in the console.
- Command-line driven / Silent Enrollment – This is the most common method for Domain Joined devices. It will leverage a “Staging” account to get the device enrolled and then “flip” to the end user that is logged in. The downside here is that you will need to deploy either via GPO or through another management tool and the device must have line-of-sight to the domain controller in order for the flip to complete.
- Autopilot/Azure Active Directory – This is the “OOBE” flow where the end-user walks through the out-of-box experience, authenticates with their corporate credentials, and then gets enrolled. This does still require an Azure Active Directory Premium license in order to do automatic MDM enrollment. There is a way to bypass the premium requirement by leveraging a PPKG as part of drop-ship provisioning.
Device Provisioning
Like Intune, Workspace ONE doesn’t have a true bare-metal imaging solution and probably never will. You will still need to leverage tools like MDT or USB provisioning to lay down Windows. You can integrate WS1 and Azure AD to take advantage of Autopilot. You can also configure one of the OEM integration solutions to have the device “provisioned” from the factory.
The first is an “offline” version where you export a PPKG of your applications and give that to the OEM. The OEM will then take that PPKG and apply it to a “generic” image in the factory. The end result is a device that comes out of the factory with your apps pre-installed. The challenge here is that you will need to pair this with Autopilot for this to be true “drop-ship” provisioning. They also have an “encrypted” PPKG option that is designed for more DIY scenarios. This will install the apps and run Sysprep with an unattend.xml file.
The second option is an “online” version where the OEM will actually power on the device in an internet-connected area, enroll it to your console, and install apps over the air. This can also include an “offline” domain join. You can pair this with VMware Tunnel and pre-logon VPN for a true drop-ship experience.
While these may sound super cool, be aware of the complexity of getting all of this set up with the OEM. Testing and ensuring all this works 100% of the time can be quite time-consuming. But with patience and attention to detail, you can get this to work and shift all of your device provisioning over to the OEM.
Unified App Catalog
One benefit of VMware owning both Horizon (VDI) and WS1 UEM is that there are some unique integrations that can be leveraged. For one, the ability to have all applications in a single catalog and presented to the end user is a big benefit. This unified catalog brings together SaaS Apps, Win32 Apps, Virtual Desktops, and virtual apps all in one place.
Cons of Workspace ONE
SaaS and Hub Upgrades can be bumpy
Running your WS1 instance as shared or dedicated SaaS means that VMware performs all of the upgrades. There are the usual “bug fix” patches as well as the major updates 3-4 times per year. The releases are marked with a YYYY.MM.Version nomenclature so you can see what version you are on by clicking on “About” in the bottom left of the console.
Generally speaking, upgrades go smoothly, but in my experience, there are often bugs or issues that crop up and must be patched later.
Additionally, each console upgrade requires that you upgrade every agent on all of the devices (iOS, Android, Windows, etc). On Windows, there is no built-in way to control this and you either have “auto” upgrade or manual. The official (but also unofficial) way to upgrade the Hub is using software distribution. You can check out my blog on how to do that.
Either way though, don’t assume that VMware has tested everything to the extent that you need. Do targeted rollouts of the Hub agent to ensure that nothing breaks and if you are on dedicated SaaS, you may want to stay on N-1 versions to ensure the smoothest rollouts.
Workspace ONE Intelligence Premium
Workspace ONE Intelligence is a cloud-based service that sits on top of your Workspace ONE console. This service provides fancy pie charts, data visualizations, third-party integrations (like ServiceNow), and in the case of Windows, Automations and Workflows.
It is difficult in my opinion to manage Windows effectively without these Automations. So things like device tagging, deploying applications or profiles based on different rules, and the new freestyle orchestrator engine are all locked behind this premium add-on. Windows environments are so complex and diverse that you need a way to deploy things with a certain level of control.
When considering whether WS1 is right for your environment, be mindful of the extra cost associated with these features. I’ve seen customers get well into production rollouts before realizing that the features they really need are included with Intelligence and they must pay up.
Windows Updates
Managing Windows Updates in WS1 is one of the least developed areas in the entire platform. The design of the Windows update profile and reporting on windows updates is very poor. In reality, you aren’t “managing” updates in the true sense at all. You are simply managing the “Policy” on the client and the client goes out to Windows Updates and patches itself. Now, this is the same as Intune, but Intune provides a lot better way of controlling the policy, feature updates, and a number of other things. WS1 doesn’t do much of that at all.
WS1 uses the “approve patch” functionality using a Windows CSP that isn’t supported for this purpose yet it is still marketed by VMware as a supported feature.
The only way to properly manage updates is to manage the client policy. Windows Update for Business is the only option here and that is what we are configuring here. This isn’t bad, per se, but it is often not even close to what is marketed and sold by VMware.
In the console, you must create a standard Windows desktop profile and select the Windows Update payload. This payload has a myriad of settings and it makes it quite difficult to understand what each does. This isn’t entirely VMware’s fault as Microsoft is the one who put in the dozens and dozens of various nobs to control Windows Update for Business. I know that the Workspace ONE team is working on improving this, but as of the time of this writing, none of the enhancements have made it to GA yet. And finally, there is no way in the GUI to control feature updates so you are stuck with creating a custom profile as detailed in my blog here.
Application Lifecycle – Automatic App Uninstall
The application lifecycle – meaning adding new versions, retiring old ones, etc. is definitely a relic of the old Airwatch days and geared more toward mobile apps. First, it is quite complicated under the hood (check out my longer blog here on this). There is a lot of hidden logic at play here. For example, when uploading an MSI the console will parse the metadata and if previous MSI versions are detected, it will automatically add a new “version” to the existing MSI app already uploaded. This can be nice, but it can also be a hassle when you want to have two different versions available to push – this isn’t possible with MSIs. If a device is in an assignment group with two versions of an MSI assigned, it will always pick the latest.
Second and more importantly, when devices unenroll ALL of their managed apps will be triggered for removal. There is no way to disable this. The only workaround is to put in a fake “uninstall” command so that when the uninstall command is triggered nothing happens. This of course means you lose out on the ability to uninstall the app, which is a bummer. Also, removing a device from a smart group with an assignment will also trigger an uninstall (again, no way to control this).
These along with limited and cumbersome “dependency” apps makes the application lifecycle for apps in Windows a challenge.
Remote Control is an Add-On Fee
VMware recently acquired a small company called “Aetherpal” and integrated its product into the UEM console as “Workspace ONE Assist”. This add-on is a basic remote control support tool that works cross-platform. While this is a functional remote support tool, this unfortunately is yet another separate add-on fee (per device) that adds to the already expensive cost of UEM + WS1 Intelligence. Mobile Jon has a more detailed write-up on whether this cost is worth it.
Dependency on Workspace ONE Access
Workspace ONE Access is VMware’s identity solution, but this isn’t a true identity provider like Okta or Ping are. WS1 Acess is more of an identity “broker”. You will be required to set up and maintain this in order to use all that WS1 UEM has to offer. It’s required for Hub Services and to get the Unified app catalog working as well as a number of other things. WS1 Access isn’t the easiest tool to use and requires a certain level of experience in identity and authentication protocols. This extra layer adds complexity to your WS1 deployment.
Pros of Microsoft Intune
Microsoft Intune is Microsoft’s flagship UEM product and they are investing large amounts of development resources toward it. There are many things to like about Intune when it comes to Windows device management.
It’s “Free”
Intune is included in so many of Microsoft’s enterprise license suites that most organizations already have it. This goes a long way in the perception of the cost of Intune. Since it’s already included in what I’m paying for Azure Active Directory or Office 365, it’s a no-brainer right? This isn’t to say that the various Microsoft bundles are cheap, but the fact that they include Intune in most of them is a great benefit.
Azure Active Directory Integration
Intune is tightly integrated into Microsoft’s cloud identity service Azure Active Directory (AAD). There is no way to get a Windows device enrolled and managed with Intune without doing one of the various Active Directory joins. The main benefit here is that you get device identity while also getting device management. Both of these are critically important and thankfully the integration here is seamless.
The two primary Azure Active Directory join types are “Azure AD only” (cloud-join) or “Azure AD Hybrid join” (domain join + azure join). There are a few different ways to achieve each, such as Autopilot, Group Policy Auto-MDM enrollment, SCCM co-management, or a bulk enrollment PPKG. A third option, called “Azure AD registered”, is available as well and is designed for a bring-your-own-device (BYOD) use case, but it isn’t as common as the other two.
Policy Management
The ability to deploy and control Windows “policy” is one of the stronger parts of Intune. It isn’t without its quirks, but overall it provides a strong platform to configure, manage, and deploy all kinds of policies to a Windows device. Many of these are native MDM policies called “CSPs”, while some are “ADMX-backed”. And recently, Intune released a way to import and deploy custom ADMX files for third-party applications.
Intune provides a number of ways to build configuration profiles in the console. The first is through the “Settings Catalog”. This is just like it sounds: a catalog of all of the various settings available for configuration on a Windows device. Simply search for a setting, tick the box to add it, and configure the values.
You can add as many or as few settings as you like. Generally, I like to create logical groups of settings such as “Security Settings” or “Windows Customizations”
Secondly, you can set up configuration profiles using “Templates”. Templates are groups of settings organized by functionality. These are things like “VPN”, “Kiosk”, or “Device Restrictions”.
Third, you can build a profile based on “Administrative Templates” which can now include custom ones you have uploaded.
And lastly, you can build a “Baseline” that includes pre-configured security settings per Microsoft’s standards. These can be a great starting place and are customizable as well.
Regardless of the method you choose, Intune has a lot of different ways to configure policy on Windows devices.
Deploying Software
Intune supports a number of app management capabilities when deploying software to windows devices. The first is deploying “store” apps through integrating Intune and the Microsoft Store for Business. This includes both online and online store apps as well as your own custom “line of business” apps. The current Microsoft Store for Business is end of life and will be replaced with a new type of distribution method. You can read more about it here.
The second method is deploying and managing traditional Win32 apps. Unlike Workspace ONE where you can directly upload an MSI or EXE file to the console, all apps in Intune must be first wrapped using the Microsoft Win32 Content Prep Tool. This tool compresses and converts the app into the “.intunewin” format. After you complete these steps, then you can upload that file to the Intune console and configure the app such as install command, detection criteria, and reboot behavior.
Intune also supports app dependencies and app supersedence as well as configuring deployment types such as “Available” or “Required”. One other benefit is that managed apps aren’t automatically uninstalled upon Intune un-enrollment, unlike Workspace ONE which will remove managed apps and does not give you a choice. I do think that making admins perform an explicit “uninstall” is the right way to go.
Device Deployment / Autopilot
Microsoft released Autopilot alongside Windows 10 as a new “modern” way to deploy Windows. Autopilot is Microsoft’s cloud-based provisioning solution that enables “drop-ship” provisioning of devices from the OEM to the user. While Autopilot is technically a standalone service, it is tightly integrated into Intune. Intune facilitates the ESP (enrollment status page), application installs, whether the device will be cloud-join or hybrid-join, and deploying policy.
Since Microsoft owns the entire stack here: the Windows OS, the Autopilot service, and Intune, they can build a much tighter integration between these products to deliver a great onboarding experience. This isn’t to say that Autopilot doesn’t have its issues, but overall Intune and Autopilot work great together and can provide a way to get out of the business of “imaging” devices on a regular basis.
Configuration Manager (SCCM) Co-Management
Microsoft Endpoint Configuration Manager (MEMCM or SCCM) can be directly integrated with Intune. This is called “Co-Management” and it means you are managing the device with two different management tools. A huge number of customers have heavily invested in SCCM and simply porting everything over to Intune is not always an easy task. Co-management allows you to control which “workloads” are managed by Intune and which stay managed by Configuration Manager.
After setting up co-management, you can control which workloads are managed by which tool with slider bars.
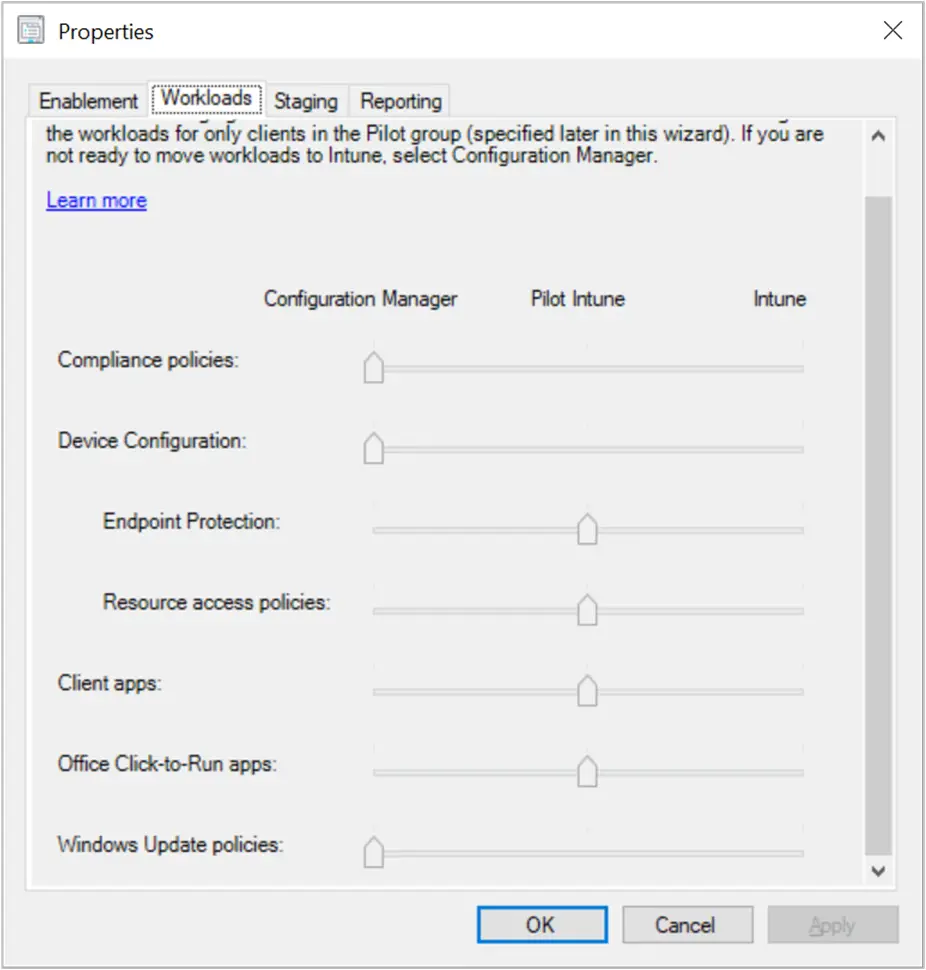
This is a unique setup that Microsoft has here; it is exclusive to SCCM and Intune. No other MDM vendor is supported or allowed to be on the device while keeping SCCM functional. If SCCM detects any other MDM vendor, it will go into “Co-existence” mode and essentially turn SCCM into “read-only” mode. While this integration is great for Intune and definitely a “Pro”, the lack of co-management support for other vendors is a big con. It puts customers in a tough spot where they have to choose between using only SCCM or their MDM vendor (like Workspace ONE).
Company Portal
Company Portal is Intune’s “self-service” portal that can be installed automatically on Windows devices. It is also available for macOS, iOS, and Android so that you get a unified look and feel. It allows users to install company apps that have been published by you as the administrator. Users can also see information about their enrolled devices, “sync” their device, and see Help Desk contact information.
Deploying the Company Portal app isn’t hard, but it does involve a number of steps. I wish Microsoft would make this a bit easier, but this is what is available today. The basic steps involved integrating the Microsoft Store for Business with your Intune tenant, adding the Company Portal to your “Private Store”, and deploying it using either the offline or online method. The general consensus that I have seen among Intune admins is that the deploying “offline” version is more reliable. Don’t worry, it will still get automatic updates from the Business store.
For a detailed walkthrough, you can check out this blog.
Heavy Microsoft Investment
There have been many rumors that SCCM is “dead” and that Microsoft is only focused on Intune. This is definitely not true as SCCM has 2-3 solid releases per year with new features constantly added. However, Microsoft is still focused heavily on Azure adoption and consumption and Intune is a critical piece to that.
Intune is developed and released more frequently than SCCM, but with smaller changes. There are major “Service” releases each month! This is all automatic and transparent to you. You will just log in one day and see that you are on the new version. Unlike Workspace ONE, there aren’t any upgrades to “schedule” or client agents to push out which makes getting the latest features seamless and easy. Here is a detailed blog by Microsoft explaining the Intune release cadence in more detail.
It’s clear that Intune is at the forefront of Microsoft’s cloud and mobile strategy and isn’t going anywhere. At Ignite 2022, Microsoft reiterated that both Intune and Configuration Manager are critical pieces of the Microsoft Intune product family.

The Community
This may be the biggest “Pro” for Intune in this whole list. Given how widespread and ubiquitous Microsoft technology is in the enterprise, there are large numbers of admins working in this space. Microsoft has the “MVP” program whereby stellar contributors can get awarded MVP status and gain access to the product group, roadmaps, and licenses. This leads to a lot of blog posts, Twitter posts, YouTube videos, and the like.
There are also numerous Microsoft user groups (often called MEMUGs) all over the country. You can meet up with other admins working with Intune on a daily basis. And to top it all off, there is the Midwest Management Summit where the very best of the MVPs and enterprise mobility admins get together and share awesome solutions, tools, and guides. The community also creates and publishes (for free!) so many different tools and solution sets to solve nearly any problem.
Cons of Microsoft Intune
Slowness
One thing you’ll immediately notice with lntune is that things don’t update or show up right away. Since Intune runs on Azure AD as a “shared” resource among all of the other tenants, Microsoft has to manage the resources that are available for processing workloads. This can’t be controlled by you the admin nor is it always clear “why” something is taking time to show up.
From deploying and assigning configuration profiles, to applications, and showing the status of items, Intune can be frustratingly slow. Even when devices first enroll they can take up to 5 minutes to show in the console. Additionally, Microsoft does have built-in throttling of requests so even if you manually click “Sync” on the client, it won’t check in more quickly than 5 minutes. And even the default Intune client sync schedule is only set to check in every 8 hours.
Reporting
Reporting in Intune, whether it’s the status of a configuration profile or an application install status, is lacking. Some profiles will report on every individual setting, while others will only report some. For example, the BitLocker profile when configured through the Endpoint Security area has dozens of settings, but when you look at the configuration profile it only shows the status of 8 of them. Other areas such as the status of cert deployment either don’t show any proper status or are extremely delayed.
Additionally, there is a confusing split on where exactly to find different reports. Some can be found under the “Reports” area while others are found under Devices > Monitor. More reports are buried under Reports > Endpoint Analytics. This makes for a cumbersome way of trying to locate which report you need and then drilling down into the right level of detail.
Policy Tattooing and other errors
Intune does a great job of applying policies to devices, but it also likes to keep them there. This is called “tattooing” and happens when a policy is set to something, such as “enabled”, and then you change the policy in Intune to “Not configured”. This essentially changes the setting to not really managed at all but Intune won’t necessarily reset it. This behavior can vary based on the CSP. Check out this Microsoft page for a bit more details, but in short, if you really want to remove a setting, assign a different profile or completely unassign it from the device and redeploy. Rudy’s blog here has some thoughts as well.
The second issue here is that many policies are ADMX-backed which means in the background, Intune must first install the ADMX file via the MDM channel and then apply the setting. But it often doesn’t get this error right and you get an “Error 65000” in the console.
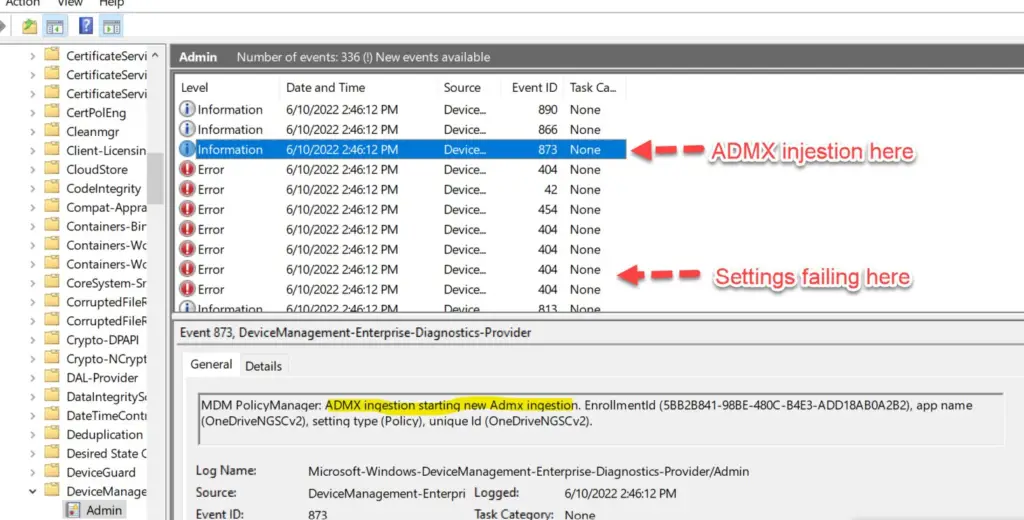
Error Reporting
Capturing and displaying helpful error codes has always been a Microsoft problem, and it’s no different here in Intune. Profiles can fail to apply for a number of reasons and the error codes reported back to the console are nearly worthless.
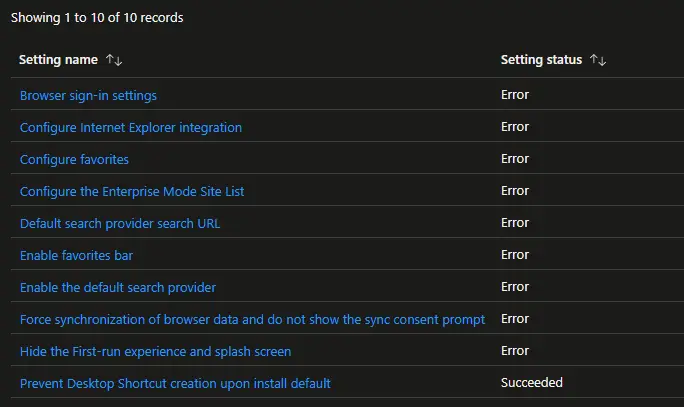
Some features that have been recently added to Intune have better error handling like custom ADMX. If you upload an incompatible node in an ADMX, it will at least directly tell you, but this is the exception rather than the norm with error reporting.
Everything requires a “Group”
Similar to SCCM and collections, you can’t deploy a workload such as an app or script to an individual device. You must first create an Azure Active Directory group (or sync on an on-prem one), add the device, and then go back and add that group to the assignment. This is more of an annoyance to how Microsoft has built both of these products, but I’d love an easier way to just push one thing to one device without having to create a whole group. A product like HLC BigFix can do this very easily and I’m a big fan of that.
Autopilot Unreliability
Check Twitter any day of the week and you’ll probably find one or more of the more active community members posting about various Autopilot errors or service outages. Whether it’s the “OOBEAADV10” error or other generic outages, the Autopilot service has been struggling as of late. It’s hard to say whether the sheer number of devices going through Autopilot is putting significant strain on the infrastructure or there are just underlying issues with the architecture, but the reliability of the service has been less than stellar. While I still think Autopilot is a great solution for most organizations, these issues may give you pause before you wholesale adopt it.
Remote Help / Teamviewer
Just like VMware, Microsoft charges extra for their version of remote control which is called Remote Help. This add-on fee can really add up if you have a lot of devices. Although recently they have announced this is now free for education customers.
Additionally, you can purchase TeamViewer separately and integrate it with Intune. While I haven’t done this personally, I have heard that this can get quite expensive. And as of Microsoft Ignite 2022, more premium add-on features are coming to Intune in 2023.
Conclusion
VMware Workspace ONE and Microsoft Intune have a number of strengths and weaknesses when it comes to managing Windows devices. It’s important to be aware of all of these when embarking on a POC or before any purchasing decisions are made.

Slight correction is needed as the below isn’t true:
“Additionally, each console upgrade requires that you upgrade every agent on all of the devices (iOS, Android, Windows, etc).”
It’s often recommended to upgrade the agents as there may be new features that require a certain UEM version to be activated but it’s not required and the agents are both forward and backwards compatible.
It also seems a little unbalanced that you call out Workspace ONE Assist as an Add-On (which is only true if you aren’t purchasing the editions that are most commonly deployed for frontline worker use cases) is a con. Yet under Intune you have it in the Pro section and MS is going to price it far higher than Assist with support for few device types and isn’t even GA yet. Not to mention that having to deploy TeamViewer means more tools for admins, while Assist is used from within WS1 and can also be exposed to ticketing systems through API.
Matt – you make a fair point. The extra add-on with Intune for remote help and/or teamviewer is also a con in my opinion due to the extra cost and in the case of TeamViewer, extra setup and cost. I’ve updated the post.
‘You can navigate to Resources > Script to upload a PowerShell script file or copy/paste the content directly.’
Is this an addon or premium feature? I don’t have the ‘Script’ option in the ‘Resources’ menu. I believe our current license is user based and is ‘Workspace One Standard’.
In response to Dale’s comment: Yeah scripting engine is offered as a part of Desktop Essentials, WS1 Advanced or Enterprise Edition. Full fledged capability of Modern Desktop management is achieved using one of the above Edition.
Sharing the WS1 feature comparison sheet – https://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/products/workspace-one/workspace-one-editions-comparison.pdf