Looking to migrate from McAfee management of BitLocker to Intune? In this blog, I’ll walk through exactly what you need to do to successfully migrate from McAfee MNE to Intune MEM for BitLocker management.
Table of Contents
- Pre-Reqs
- Summary of Steps
- Create a Policy Assignment in McAfee ePO for “Report Only” Mode
- How to Apply Tag to a Device
- Backing up BitLocker Recovery Key
- Deploy Intune Migration Script
- Conclusion
Pre-Reqs
In my setup, I’m working in the following conditions although other variants of this should work fine:
- McAfee ePolicy Orchestrator 5.10.0
- MNE agent 4.1.5.3
- McAfee Agent 5.7.6.251
- Devices are Windows 10 Hybrid Azure AD Joined
- Devices are co-managed with SCCM, but the BitLocker workload is managed by Intune
Summary of Steps
- Create a Tag and assign a policy in EPO
- Configure tag to apply based on a custom property
- Deploy PowerShell script
Create a Policy Assignment in McAfee ePO for “Report Only” Mode
You will need to work with your McAfee ePO administrator on this step, but essentially what they need to do is to create a policy that configures McAfee MNE policy to go into “Report Only” mode. This means that it will continue to report on the status of encryption on the device, but it won’t actively manage or enforce BitLocker. Then you will create a tag and assign this policy to that tag. And finally, we’ll assign the tag to devices by leveraging a custom attribute that can be applied to the device via command line.
First, create a “Report Only” mode policy. Here’s how you can do this:
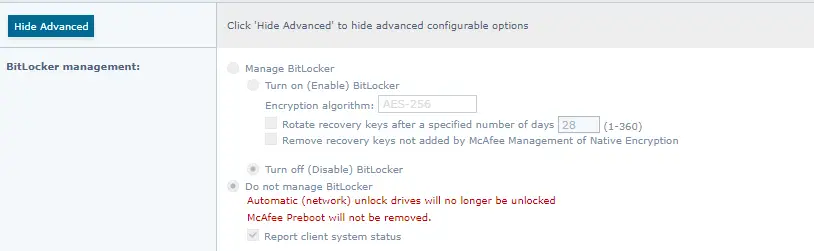
- In McAfee ePO, go to Policy Catalog and select Management of Native Encryption.
- Create a new Policy and name it.
- Configure it with Do not manage BitLocker.
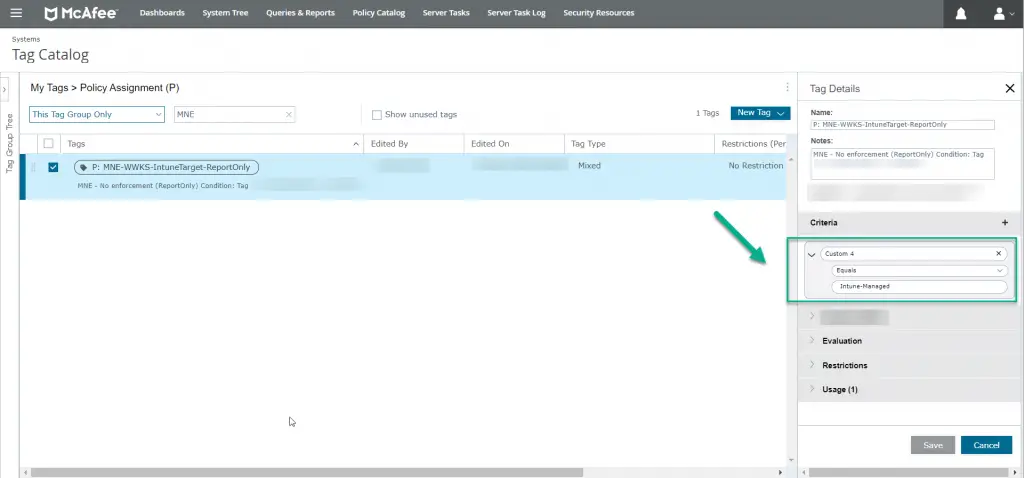
Next, we need to create a new tag in the Tag Catalog area and assign the policy to it. You can read more about how to do this in McAfee’s article here.
On the tag details, under the criteria section, we chose to leverage custom property 4 since it wasn’t in use by anything. When a device gets custom property 4 set to “Intune-Managed”, this tag will automatically apply which will, in turn, assigns the “Report Only” profile.
How to Apply Tag to a Device
Applying the tag to the device can be done with a few lines of code. We target C:\Program Files\McAfee\Agent\maconfig.exe and pass the parameters -custom -prop4 Intune-Managed to it. After that we run Collect/Send props a few times and then the client will get the updated policy. This code is also included in the full script which is available at the end of the blog.
#Tag System Intune Enrolled
Start-Process "C:\Program Files\McAfee\Agent\maconfig.exe" -ArgumentList "-custom -prop4 Intune-Managed" -Wait -RedirectStandardOutput c:\temp\McafeeBitLockerTag.log
Sleep -Seconds 10
#Collect/Send Props
Start-Process "C:\Program Files\McAfee\Agent\maconfig.exe" -ArgumentList "-p" -Wait
Sleep -Seconds 60
#Collect/Send Props
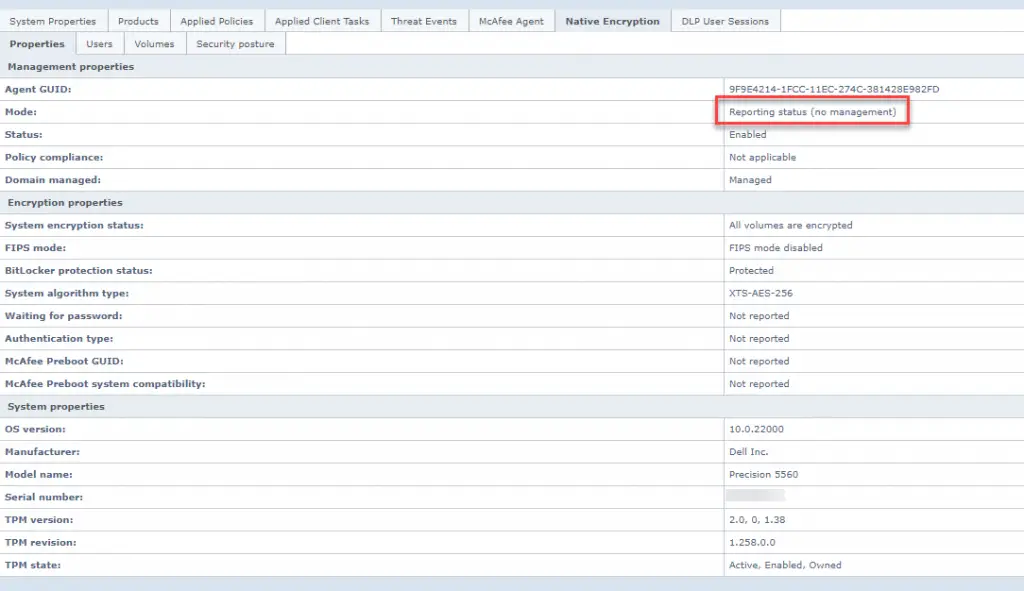
Start-Process "C:\Program Files\McAfee\Agent\maconfig.exe" -ArgumentList "-p" -WaitOnce you apply the property to a device and it gets the updated policy, it will look like this:
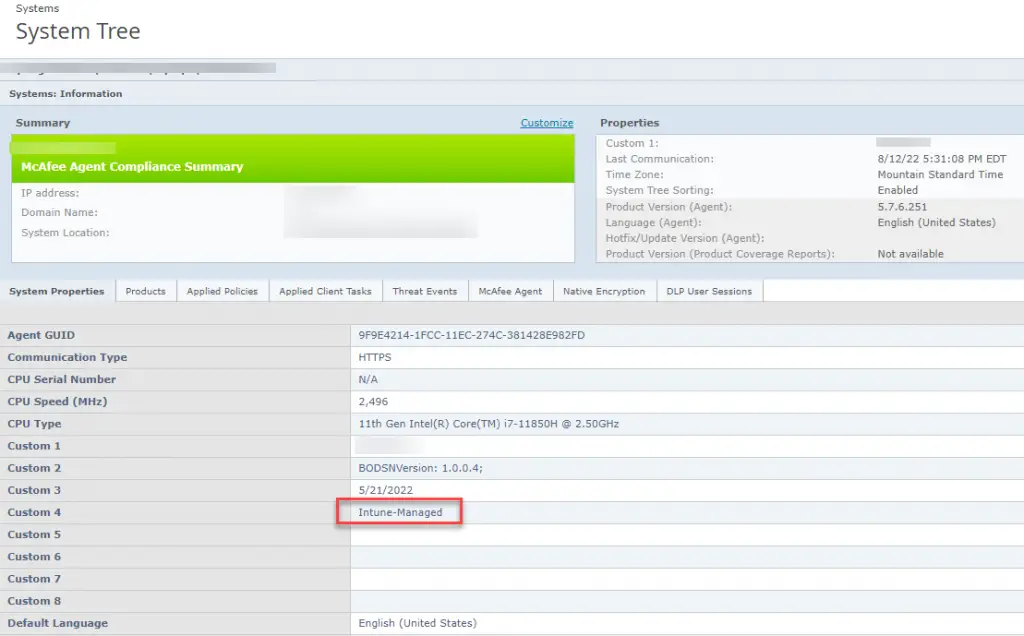
Tag Applied
Backing up BitLocker Recovery Key
Since your devices are already encrypted with BitLocker, you will still have to manually backup the key to Azure AD. Thankfully you don’t need to fully decrypt and re-encrypt the device unless, of course, you want to change the encryption algorithm. The command to backup the key is a few lines of PowerShell and is also included in the main migration script.
$BLV = Get-BitLockerVolume -MountPoint "C:" | select *
[array]$ID = ($BLV.KeyProtector | Where-Object { $_.KeyProtectorType -eq 'RecoveryPassword' }).KeyProtectorId
BackupToAAD-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId $ID[0]You can read more about this on my other blog.
Deploy Intune Migration Script
Let’s put this all together now. I put together this PowerShell script that will do everything we have talked about:
- Checks and verifies the system is enrolled into Intune.
- Verifies the Intune BitLocker profile is successfully applied to the device (by checking reg keys). I don’t want to migrate a system if it hasn’t yet received the Intune policy.
- Backs up the BitLocker key to Azure AD
- Ensures MNE service is still running
- Applies the McAfee custom property using maconfig.exe
- Applies a reg key to “stamp” the device that it has been migrated (optional).
Simply deploy the script via Intune, Configuration Manager, or another management tool to get your systems migrated.
Conclusion
We first set up a policy for “Report Only” mode and then created a Tag for the assignment. We then configured the tag to apply to systems with a custom property of “Intune-Managed”. Then we added all of this to a PowerShell script which in turn backs up the BitLocker Key to Azure AD, applies the tag to the device, and updates the McAfee policy to no longer manage Bitlocker on the device. Now you know how to migrate from McAfee Management of Native Encryption to Intune for managing BitLocker.
