Has your organization raised concerns about end users having the ability to retrieve their own BitLocker keys? In theory, this is a great way to reduce help desk calls and improve user experience, but it does raise the question of whether this is a security risk or not. Until now, Microsoft hasn’t had a way to restrict this.
This month (August 2022), Microsoft finally released a new Azure AD permission that can lock this down for your end users. In this blog, we’ll walk through how to implement this so that you can prevent your end users from accessing their own BitLocker keys
Table of Contents
- How does BitLocker Recovery Key Self-Service work?
- How to Block Users from Accessing BitLocker Keys
- Test it Out
- Further Reading
How does BitLocker Recovery Key Self-Service work?
If you are newer to Intune and AAD or just haven’t implemented BitLocker yet with Intune (which by way, definitely check out this blog before you begin), end users are able to retrieve their own BitLocker keys by going to their “My Account” page. On their Intune-managed device, they can navigate to myaccount.microsoft.com.
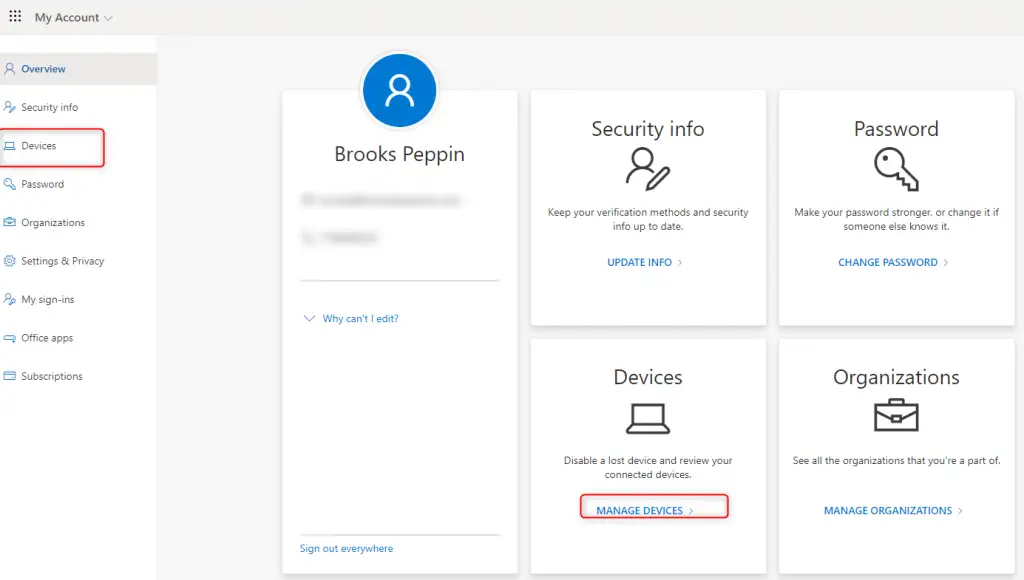
Note that this page is also visible on an Intune-managed mobile device (iOS/Android) so even if an end user’s main device is locked by BitLocker, they can see the keys on their mobile device. Additionally, devices must be properly assigned to them as the “Primary User”.
Additionally, users can click on View account from their Office 365 account page which will also bring them to the same My Account page.
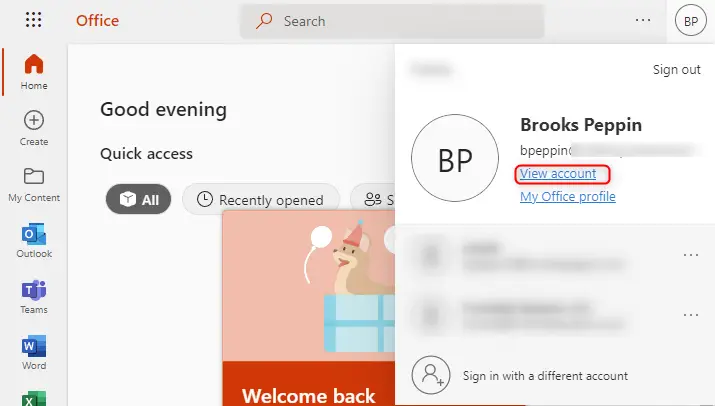
This area does a lot more than just grant access to BitLocker keys of course, but to view keys they just have to click on manage devices, find their device, and click on view BitLocker keys.
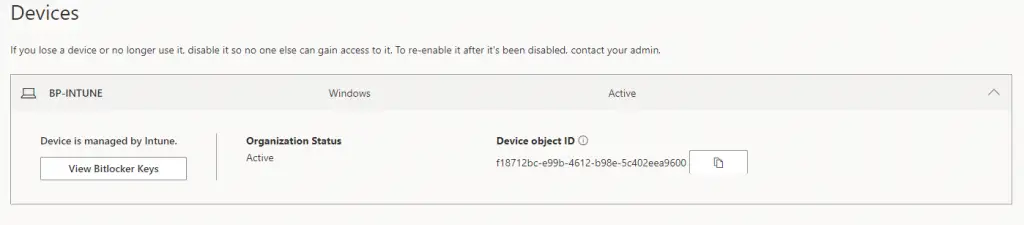
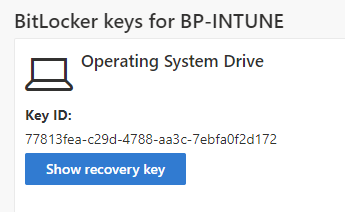
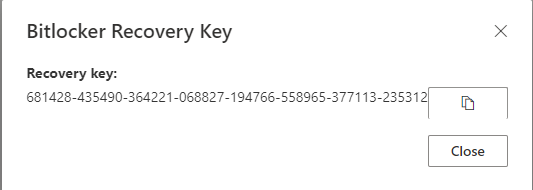
Now that we know how to access BitLocker keys via Self-Service, let’s walk through how to disable this.
How to Block Users from Accessing BitLocker Keys
Microsoft has now added a way to turn off the “View BitLocker Keys” button for all users by running a pretty simple Graph API command. There are a few pre-requisites and details you should know about before running this.
- It technically still is in “preview”
- End users that have been explicitly granted rights to read BitLocker keys in Azure will still be able to see their keys. Roles such as Security Reader, Global Reader, etc. grant this.
- The admin running the script will need to have Policy.ReadWrite.Authorization write permissions in Azure AD.
- Since the script will be running Graph commands, you will need to have the “Microsoft.Graph” module installed on your device.
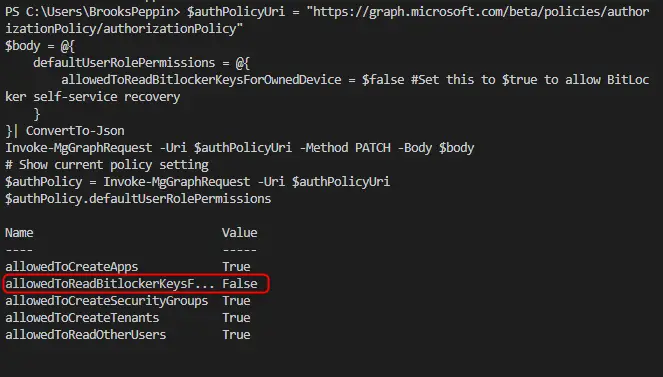
Here is the code you need to run that was provided by Microsoft on the docs page:
Connect-MgGraph -Scopes Policy.ReadWrite.Authorization
$authPolicyUri = "https://graph.microsoft.com/beta/policies/authorizationPolicy/authorizationPolicy"
$body = @{
defaultUserRolePermissions = @{
allowedToReadBitlockerKeysForOwnedDevice = $false #Set this to $true to allow BitLocker self-service recovery
}
}| ConvertTo-Json
Invoke-MgGraphRequest -Uri $authPolicyUri -Method PATCH -Body $body
# Show current policy setting
$authPolicy = Invoke-MgGraphRequest -Uri $authPolicyUri
$authPolicy.defaultUserRolePermissionsLet’s step through this.
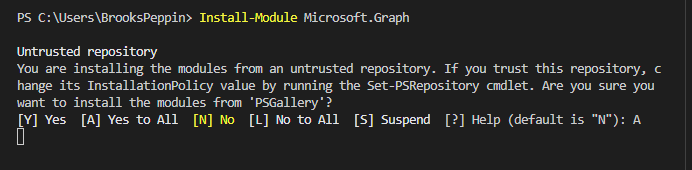
First, run PowerShell as administrator and install the Microsoft.Graph PowerShell module.
Install-Module Microsoft.GraphWhen prompted to install modules from the PSGallery, type Y or A.
This will install around 38 different sub-modules. After this completes, run the first line of the script to connect to Graph.
Connect-MgGraph -Scopes Policy.ReadWrite.AuthorizationYou will then be presented with an authentication screen. Enter your credentials and any MFA to continue.
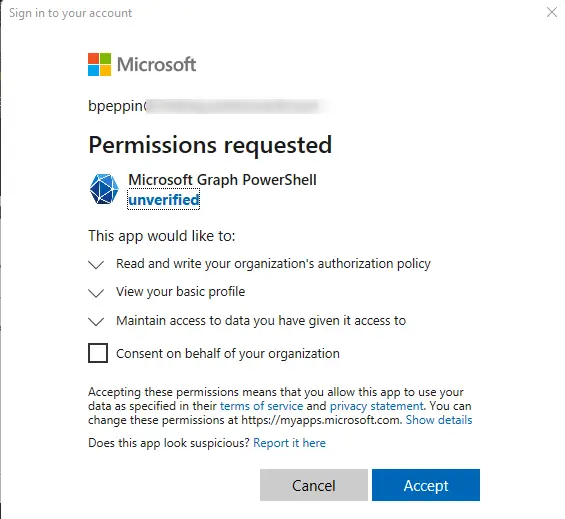
You will then come to the Microsoft Graph PowerShell permissions screen. You will need to accept these permissions and optionally “consent on behalf of your organization”.
After that, run the remaining lines of the script to change the allowedToReadBitlockerKeysForOwnedDevice permission to false.
Test it Out
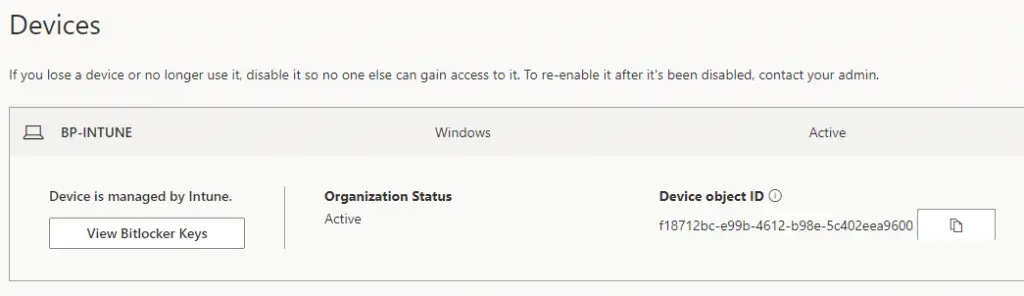
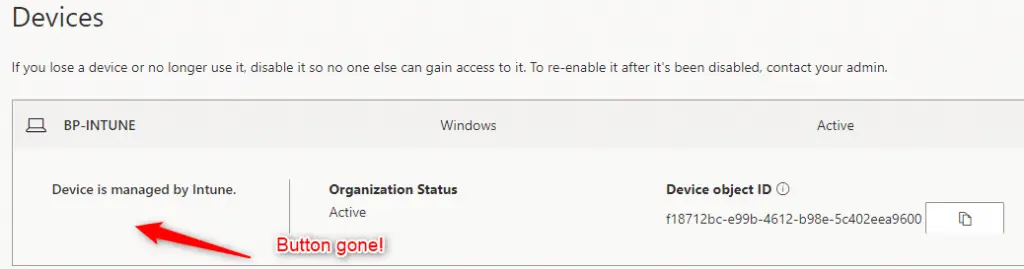
Now refresh the My Account page and the View BitLocker Keys button will be removed.
Before:
After:
I’m glad that Microsoft finally added the ability to control access to BitLocker recovery keys via Self-Service. In many organizations, this will help keep data more secure by not allowing end users to decrypt data if they aren’t meant to.
Further Reading
For further reading on how to implement BitLocker management with Intune, check out my other blogs:
3 Things You Should Know Before Deploying BitLocker with Intune
A Beginner’s Guide to Managing BitLocker with Intune
How to Migrate from McAfee MNE to Intune for BitLocker Management
Thanks Brook. Does this only work on devices enrolled in Intune or just generally any device that’s joined to Azure AD (OOBE and/or enrolled with another MDM) with bitlocker keys available to the user?
Since this is an Azure AD setting, then it works on any device that is joined to Azure (Either cloud joined or Hybrid). MDM doesn’t matter or apply in this case.